Attention! According to Astra statistics, 2200 cyber attacks happen per day. Effective cyber defense is undoubtedly essential today. When you are under a cyber attack, saving your assets and identity is difficult. So what must be done? Action to prevent is the key.
Let’s explore the 5 critical tenets of effective cybersecurity defense with us:
Transport Layered Security(TLS)
When discussing layered security, we are talking about defense in depth. Layered security is a cybersecurity strategy that businesses and organizations implement to protect systems and data.
Because of this mode of security, it becomes difficult for attackers or hackers to breach the defenses.
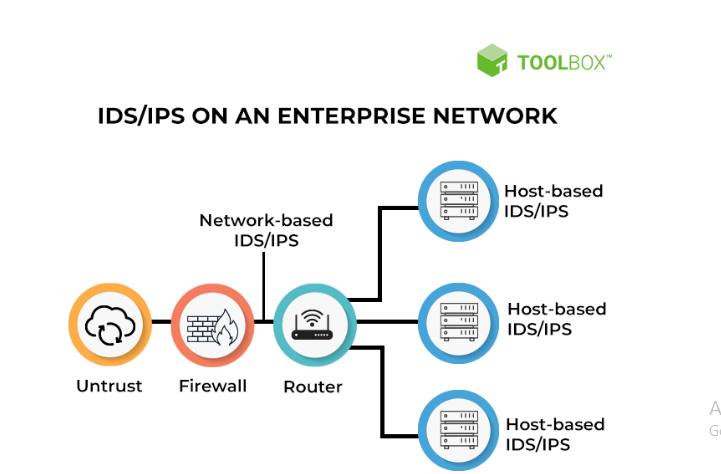
In this defense, different techniques are being used. These include.
- Intrusion Detection and Prevention Systems – (IDPS ) systems monitor network traffic and find signs of malicious activity. Once they catch something, they automatically block or alert administrators about potential threats.
- VPNs – VPNs are known to establish secure and encrypted connections between you and servers. A reliable VPN ensures that data transmitted over the internet remains secure.
- Network Segmentation – It’s a powerful defense used by businesses where a network is broken into smaller segments to help contain potential breaches. Even if an attacker gains access to one segment, they will find moving laterally to other network parts challenging.
- Email Filtering – Scams are getting the best out of businesses. Filtering incoming emails to check for spam, phishing attempts, and malware helps prevent organizations from interacting with malicious content.
Continuous Monitoring
Continuous monitoring is a potent cyber defense that involves observing an organization’s systems, networks, and applications. The purpose is to detect and respond to security threats and vulnerabilities in real-time. No one underestimates the importance of periodic security assessments, but at the same time, continuous monitoring is far better for identifying hazards.
There are different monitoring tools that organizations and businesses use, and these include.
- Real-time Threat Detection – Monitoring tools are always working where they are used as a defense. They constantly analyze network traffic, system logs, and other data sources. The purpose is to identify patterns that indicate the potential security breach or intrusion. With these tools, teams respond quickly before significant damage occurs.
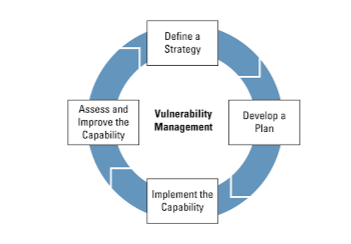
- Vulnerability Management – Same as real-time, vulnerability tools can scan systems and applications for known vulnerabilities and misconfigurations. Once the organization identifies the weaknesses early on, it can apply patches and updates to reduce the risk of exploitation.
- Behavioral Analysis – Some monitoring tools use machine learning and artificial intelligence for behavioral analysis. These tools establish a baseline of normal behavior for systems. Deviations from this baseline can indicate unauthorized access or malicious activity.
- Automated Responses – Businesses often make sure of different monitoring tools that can trigger automatic responses to specific events. For example, if a device detects multiple login failed attempts, it will automatically block further access attempts from that source.
3:Timely Patching
Timely patching is another critical cybersecurity practice. This practice involves regularly updating software, applications, operating systems, and other technology components with the latest security patches.
These patches are often released so businesses can address vulnerabilities and weaknesses that attackers can exploit to compromise systems, steal data, or cause disruptions.
There are several tools for this purpose as well, and these include:
- Vulnerability Scanners – These help scan systems and applications so they can identify known vulnerabilities. Scanners provide a list of missing patches and updates that must be applied.
- Operating System Update Services – As technology evolves, many operating systems come with built-in mechanisms for automatic updates. These mechanisms ensure that the Operating system receives the latest security patches without requiring manual intervention.
- Automated Patch Deployment – These tools provide the best cyber defense because they schedule and deploy patches during off-peak hours. This minimizes disruptions to regular operations.
- Endpoint Detection and Response Solutions – Such tools provide timely patching management. They focus on monitoring and protecting devices within a network to detect malicious activities.
Red Teaming
Red teaming is a wonder in a cybersecurity practice. It involves simulating real-world attacks on systems, networks, and applications. Red teaming helps in the identification of vulnerabilities and weaknesses.
Unlike conventional security assessments, red teaming focuses on mimicking the techniques of actual threats. This cyber security defense practice involves ethical hacking as well.
Common tools that are used in red teaming involve:
- Social Engineering Toolkit is highly effective in creating and executing social engineering attacks. There can be a simulation of phishing emails and malicious websites.
- Responder – To catch a killer, you have to think like one. Responder is a tool that helps in collecting credentials. It is particularly useful for testing the effectiveness of password policies.
- Network Analyzer -Network protocol analyzer which are extremely effective in analyzing network traffic. They help identify vulnerabilities and understand network behavior to curb potential cyber attacks.
- Scanners – Vulnerability scanners are used by red-teeming experts to identify weaknesses in systems and applications.
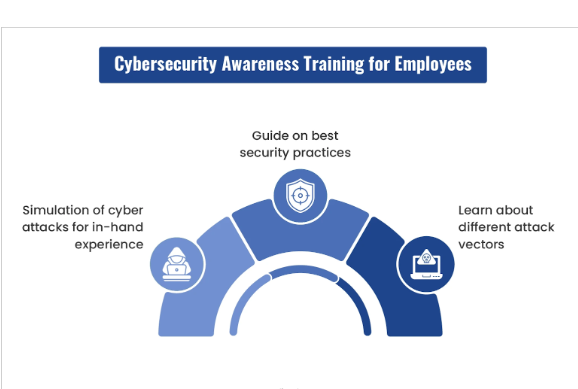
Employee Training and Awareness
Human error is often a prominent factor in cyber incidents. Companies or businesses must provide regular cybersecurity training to raise cyber threat awareness.
Employees need to understand how to recognize phishing attempts and secure their passwords to follow best practices for data protection.
An intelligent workforce can act as an added layer of defense against various cyber threats. To train and aware employees, these tools can be used:
- Phishing Simulators – These brilliant tools can create mock phishing email campaigns. This aims to test employees’ ability to identify and report suspicious emails. Such emulators provide immediate feedback and help raise awareness about phishing risks.
- Cybersecurity Workshops and Webinars – Businesses can organize regular workshops and webinars by cybersecurity experts to help employees stay updated on the latest threats. These experts can also teach about attack techniques and best practices for safeguarding data.
- E-Learning Platforms – Such online learning platforms are ideal for learning about the latest cybersecurity courses that eventually help with cyber security.
- Scenario-Based Training – This training also mimics real-world cybersecurity situations employees may encounter. Eventually, this helps them practice responding appropriately to threats.
Prevention is better than Cure
The world is turning into a tech hub. Because everything is going online, the prospect of cyber threats is valid. But every problem has a solution, and that is where cyber defenses come in.
It is optional to constantly learn from experience because sometimes prevention is better than cure. You can use mentioned cyber threat defenses in real life to protect yourself from Cyber attacks.
Author Bio:
Anas Hassan is a tech geek and cybersecurity enthusiast at PureVPN. He has vast experience in the field of digital transformation industry. When Anas isn’t blogging, he watches the football games.







